Demystify Hybrid-Join
- Viktor Ahorner
- Aug 23, 2022
- 5 min read
Updated: Oct 8, 2023


Microsoft has integrated Windows Hybrid-Join with Windows10 Version 1706. Since there alot of features and new capabilities have been added. I will try to explain all important key facts and information about this technology, so that you have a full overview and can deal with it in your organisation.
What is hybrid-join?
Simply explained, is hybrid-joined “Computer”: A synchronized computer object from “Local” Active Directory to Azure Active directory. Computer-Objects are matched by DeviceID and can access Cloud and On-Prem resources without VPN.

Why do you need hybrid-join?
If you have a big enterprise environment with a big on-prem infrastructure and you are not able to go “Cloud-Only”(Autopilot), you need to deploy hybrid-join to be able to manage your On-Prem Computer / Servers from Microsoft Endpoint-Manager.
Hybrid-join is one of most common used conditions for Azure AD Conditional Access. This option enables secure access to your cloud-resources only from domain managed clients.

Hybrid-join is one of pre-requisites if you want to use Microsoft Endpoint manager as MDM authority for your endpoints. This gives you a possiblity to manage
- Devices
- Device configurations
- Software
- Software configurations
- Security / Compliance settings
- Reporting
For all your Domain-Joined devices from the cloud.
Hybrid-join is also a pre-requisite to on-board Windows Defender for Endpoints.
Hybrid-join is also required for enabling Windows Hello 4 Business.
How can computer object be synchronized to Azure AD?
Most important and critical thing to know is, that you can configure only ONE AzureAD connector each tenant! And only ONE write back AD forrest!
Single forest
For a single forest AD you can use “simply” Azure AD connect.

If you have a federation provider like ADFS, or PING federate (or any other federation service), you can activate “Device Registration” to automate Computer-Object “synchronization” process.

Multiple forests
For a multiple forest environment there are a lot of creative solutions how to bring you computer objects into Azure AD. I will try to explain 3 most compliant and used scenarios:
Domain trust scenario (Kerberos trust)
The most uncommon and simple scenario is, to trust all forests with each other and configure one AzureAD connector from the “main” forest.

Sync all forests to one scenario (Group / Main forrest)
In this scenario all forests are syncing AD objects using MIM (Microsoft Identity manager) to one “main” AD and from this AD, all objects are synchronized to AzureAD using AAD-Sync (AzureAD Synchronization).
From my perspective this is the most comprehensive and common architecture for hybrid-join.

Sync all forests to one and use federation service for device registration
In this scenario Computer-Objects are not synchronized via AAD-Sync. Every single forest is connected to one federation service. Federation service is registering all Computer-Objects into Azure AD. Only users are synchronized to via AAD-Sync to be able to use cloud services.
This is the most complex and flexible solution for hybrid-join.

What are main infrastructure requirements for hybrid-join?
Operation system:
- Windows 10 (1706)
- Windows Server 2016 (1706)
- Windows Server 2019 (1706)
Windows scheduled task:
- GoTo Windows “Task Scheduler”
- GoTo Microsoft > Windows > Workplace Join


Make sure that this task is persisting and has valid triggers.
In some cases this task is disabled. This doesn’t mean that it is not runing. This means that this task can not be scheduled, but still running on “login” event mostly.
Service connection point:
Service connection point (SCP) is located in configuration of directory schema (mostly) and can be configured in 3 different ways:
- AzureAD connect (by clicking enable hybrid-join)
- GPO
- Simple registry entrée
For exact information, read hybrid-join scp documentation from Microsoft.
Following SCP script is provided by Microsoft for proper integration.
$verifiedDomain = "contoso.com" # Replace this with any of your verified domain names in Azure AD
$tenantID = "9b511fda-f0b1-43a5-b06e-12345678" # Replace this with any of your own tenant id
$configNC = "CN=Configuration,DC=corp,DC=contoso,DC=com" # Replace this with your Active Directory configuration naming context
$de = New-Object System.DirectoryServices.DirectoryEntry
$de.Path = "LDAP://CN=Services," + $configNC
$deDRC = $de.Children.Add("CN=Device Registration Configuration", "container")
$deDRC.CommitChanges()
$deSCP = $deDRC.Children.Add("CN=62a0ff2e-97b9-4513-943f-0d221bd30080", "serviceConnectionPoint")
$deSCP.Properties["keywords"].Add("azureADName:" + $verifiedDomain)
$deSCP.Properties["keywords"].Add("azureADId:" + $tenantID)
$deSCP.CommitChanges()Connection requirements:
Hybrid-Join is using HTTPS connection outbound, so make sure that your computer can reach your following endpoints using port 443 and SSL inspection is disabled. If you have a proxy based on user ACL, this scheduled task is runing as NT System account and not as logged user
- Make sure that your computer can reach your DNS server by using port 53
- Make sure that your computer can reawch your domain controller by using port 389
- If you use federation service make sure, that your clients can reach this by using port 443 without any ssl inspection
For succesfull hybrid join, computer needs to reach domain controller and azure endpoints without ssl inspection , either it will not work.
How to check if device is hybrid-joined?
You can us “dsregcmd /status” command for checking hybrid-join status.
You can us “dsregcmd /join” command for manual join.
You can us “dsregcmd /leave” command for unjoin. (This command can be used for troubleshooting of hybrid-join. After leave it will automatically join again as soon scheduled task run again sucessfuly.
DSREGCMD /status explained
If you device state has BOTH AzureADJoined and DomainJoined to Yes, your device is successfully hybrid-joined.

Here you can see device ID and TPM information. If TPM chip isn’t working well, hybrid-join will not work.

Here you can see tenant information.

Sometimes SCP has different tenant information as in DSREGCMD /status and hybrid-join is not working
All other status points are mostly related to User authentication, SSO (single sign on) and PRT (primary refresh token). This is mostly used by “Conditional Access”



How to troubleshoot hybrid-join?
Most issues with hybrid-join are related to connectivity, so before you start to troubleshoot anything, check all requirements in this article.
How to check?
Remember that hybrid-join scheduled task is always running as NT-System user. So, you need to troubleshoot any connection issue as SYSTEM USER and not as LOGGED user. To do this, use PS-TOOLS.
Eventlog
All events are located in event logs.
Open eventvwr > Application and Servicelogs > Microsoft > Windows > User device registration

AzureAD status
You can check hybrid-join device status in Azure AD.
So just login into https://portal.azure.com
GoTO Azure Active directory > devices
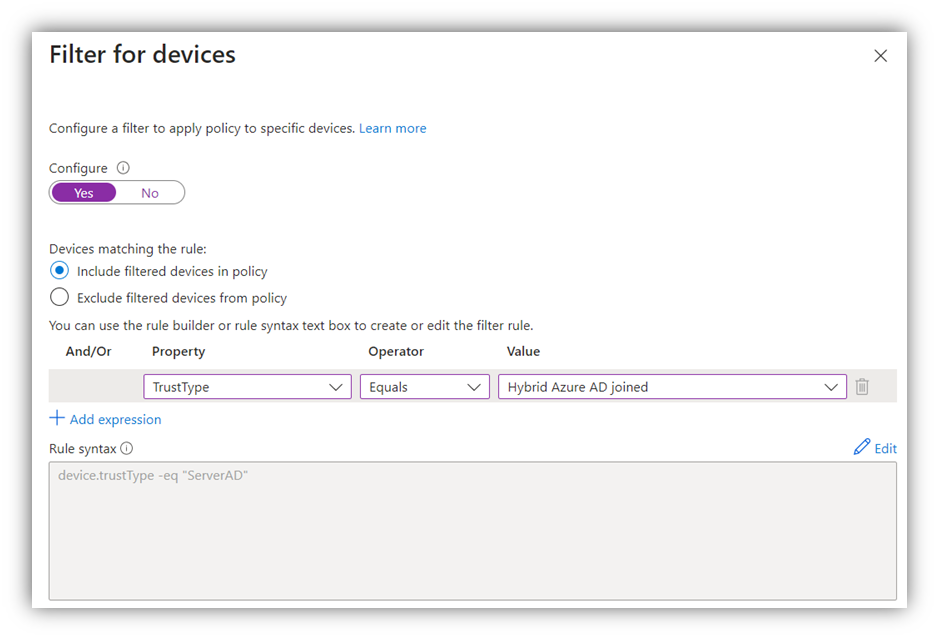
Filter devices by “Join Type” > “Hybrid-Azure AD joined”
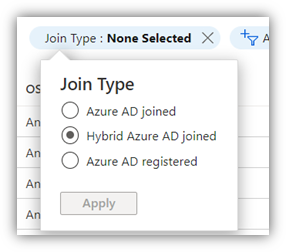


Be aware that only devies with a valid registration date are fully hybrid-joined.

Devices with status “Pending” are still waiting for write-back to local AD forrest.
You can also use powershell to check hybrid-join status.
Get-AzureADDeviceWith this Scriptline you can easy get all Hybrid-Joined devices from your AzureAD
Get-AzureADDevice |?{$_.DeviceTrustType -eq 'ServerAd'} | select DisplayName, DeviceTrustType, DeviceOSType, IsManaged 
I hope you have enjoyed this demystification article.
If you have any questions just leave me a feedback.

Kommentarer